This single processor demo application shows how to do the TrustZone Partitioning. It is split into a secure and non-secure part. Using CMSIS-Zone, it generates:
The application itself shows how to implement calls between the secure and the non-secure part.
The STM32L5.azone file of that project has the following configuration settings:
blinky_s and blinky_ns CODE_NS, CODE_S, Veneer, DATA_NS, and DATA_S 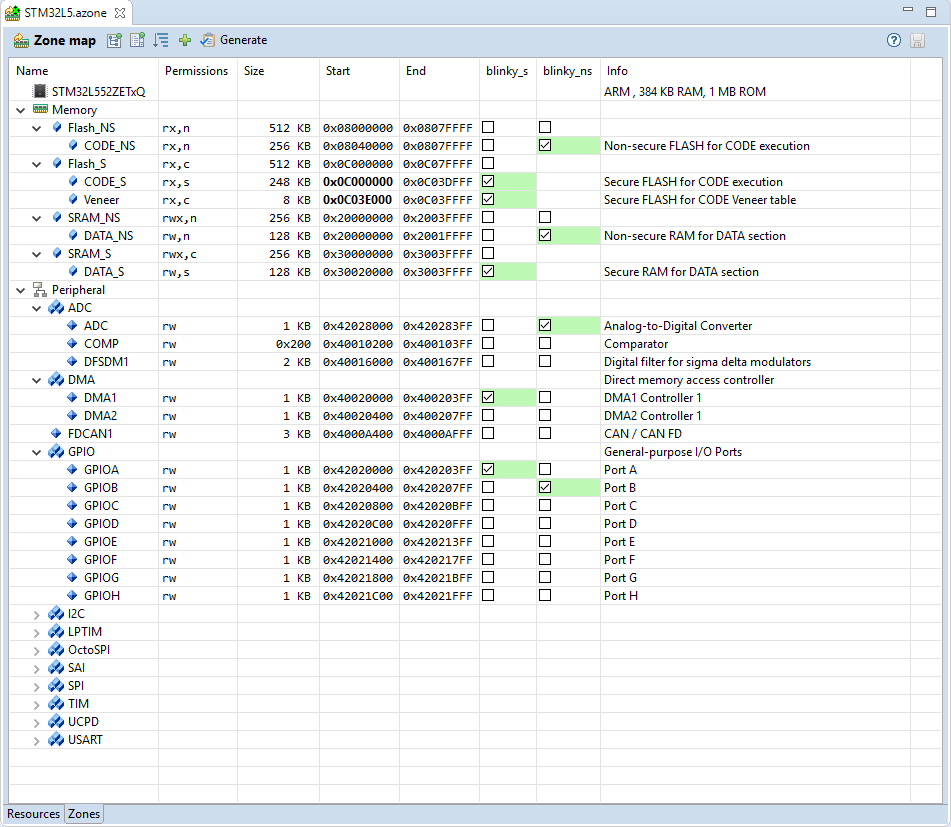
The zones use different Flash and SRAM regions for code and data, but share Flash configuration registers. Peripherals, such as the system and IO configuration, as well as an UART are available in the secure world only. To generate the output, click on the Generate button in the Zone Editor tool bar. This creates the following files in the ftl_gen directory:
| Template File | Generated File | Description |
|---|---|---|
| dump_fzone.txt.ftl | dump_fzone.txt | Contains the complete model |
| helper.ftlinc | N/A | Helper template file with FTL functions. |
| mem_layout.h.ftl | mem_layout.h | Header file that contains the memory region definitions, for example for the linker scatter file. |
| partition_gen.h.ftl | partition_gen.h | Configuration of the secure attribution unit (SAU) and the NVIC interrupt assignment. |
| SystemIsolation_Config.c.ftl | SystemIsolation_Config.c | Setup of the MPC and PPC. |
| scatter_ns.sct.ftl | scatter_ns.sct | Example scatter file for non-secure zone. |
| scatter_s.sct.ftl | scatter_s.sct | Example scatter file for secure zone. |
These files can be used in any IDE to create the final application. In the following, the usage in Arm Keil MDK is described.
The example project can be loaded, built and debugged in µVision by performing the following steps:
The multiproject workspace contains the secure blinky_s project and the non-secure blinky_ns project:
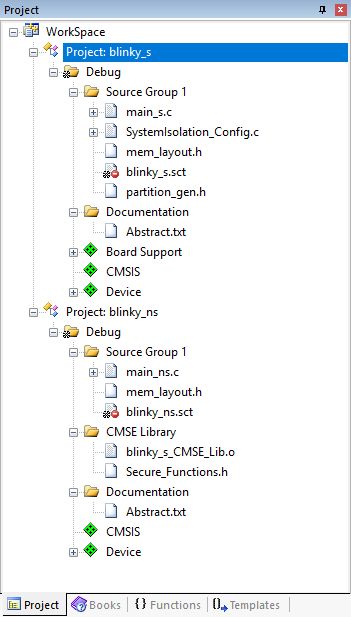
The projects use the files generated in CMSIS-Zone as follows:
| File | Used in | Description |
|---|---|---|
| mem_layout.h | blinky_s, blinky_ns | Input for the linker scatter files. |
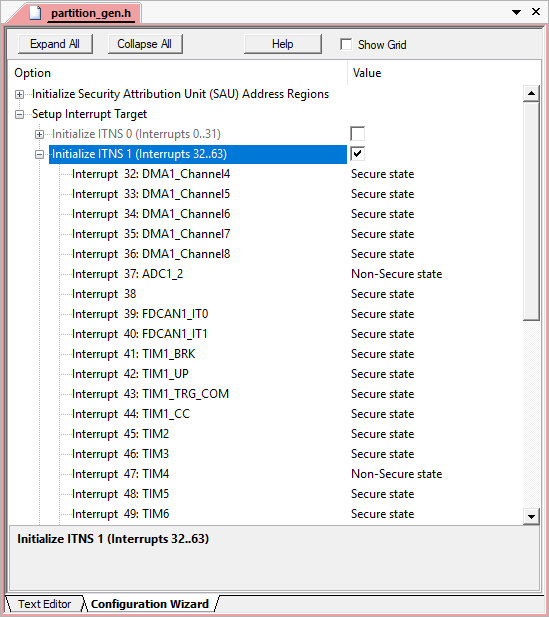
| partition_gen.h | blinky_s | Configuration of the secure attribution unit (SAU) and the NVIC interrupt assignment. This file is included in the partition_stm32l5xx.h header file. |
| SystemIsolation_Config.c | blinky_s | Setup of the MPC and PPC. |
| blinky_ns.sct | blinky_ns | Scatter file for non-secure zone (initally based on generated file). |
| blinky_s.sct | blinky_s | Scatter file for secure zone (initally based on generated file). |
As explained previously, the #defines in mem_layout.h can be used to create generic scatter files that are easy to update once changes in the CMSIS-Zone project happen. Using the mem_layout.h file from CMSIS-Zone, the following scatter file is used in the secure blinky project, which is based on the generated scatterf file (scatter_s.sct):
The partition_gen.h header file contains Configuration Wizard annotation so that it can be viewed in a graphical window: