 |
CMSIS-Zone
Version 1.2.0-alpha
System Resource Management
|
 |
CMSIS-Zone
Version 1.2.0-alpha
System Resource Management
|
This example shows how to do the TrustZone Partitioning. It is split into a secure and non-secure part. Using CMSIS-Zone, it generates:
The Musca-A1.azone file of that project has the following configuration settings:
SecureFW and NonsecureFW SecureRAM, NonsecureRAM, ScureCode, Veneer, and NonsecureCode 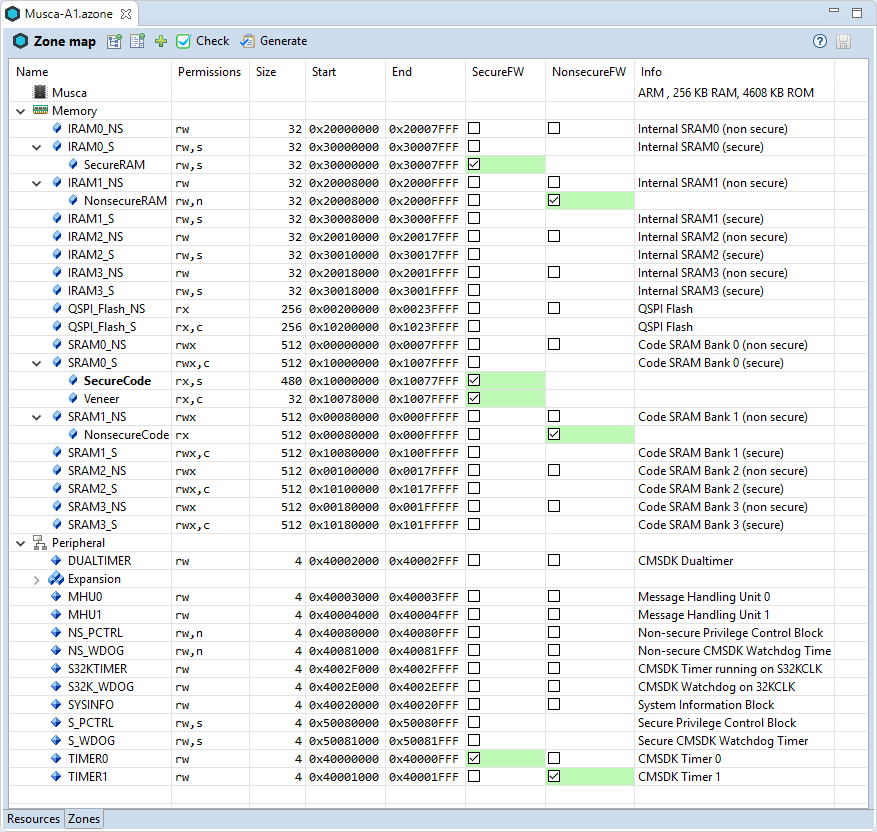
The zones use different Flash and SRAM regions for code and data. Peripherals, such as the system and IO configuration, as well as UART0 are available in the secure world only. To generate the output, click on the Generate button in the Zone Editor tool bar. This creates the following files in the ftl_gen directory:
| Template File | Generated File | Description |
|---|---|---|
| dump_fzone.txt.ftl | dump_fzone.txt | Contains the complete model |
| helper.ftlinc | N/A | Helper template file with FTL functions. |
| mem_layout.h.ftl | mem_layout.h | Header file that contains the memory region definitions, for example for the linker scatter file. |
| tz_sau_nvic.c.ftl | tz_sau_nvic.c | Configuration of the secure attribution unit (SAU) and the NVIC interrupt assignment. |
| tz_mpc_ppc.c.ftl | tz_mpc_ppc.c | Configuration of the memory (MPC) and peripheral (PPC) protection controller. |
These files can be used in any IDE to create the final application.