In today's world, secure communication is crucial for many applications to protect data transmission between two network nodes. The Transport Layer Security (TLS) protocol is a standardized technology for establishing a secure, encrypted and authenticated link between two parties over an insecure network. TLS is an industry standard and is used in millions of devices and websites.
The Network component offers two ways to secure communication in an application:
Although the Network component does not offer encryption and secure communication on its own, you can use Arm's mbed TLS software component to achieve this.
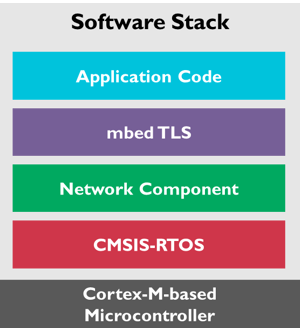
From the bottom up:
The Mbed TLS library is designed for ease-of-use. The library is documented and has examples so you can easily understand how to use it. In the Network Component, Mbed TLS is used under the Apache 2.0 license, enabling you to use it in both open source and closed source projects. Mbed TLS is a fully featured and standards compliant SSL library offering server and client functionality in one single package.
The TLS protocol is the successor of the SSL protocol. Just like its predecessor, the TLS protocol provides communication security for connections over possibly untrusted networks, like the Internet. The main difference between TLS and SSL is the increased standardization of the workings of the protocol. SSL itself was designed and developed by Netscape. The newer TLS standard is defined in a number of public RFCs and is extended periodically to counter possible weaknesses or add much needed functionality.
In order to perform the SSL or TLS protocol, a number of supporting functionality is required. The SSL/TLS library:
All of this is hidden from most users and wrapped inside an SSL library, such as Mbed TLS, which developers can use to implement SSL or TLS in their applications.
For more information on Mbed TLS and how it works, visit the high-level design overview page.
The Examples section carries two examples for secure communication over the IP network: SSL Server and SSL Client. To use the Mbed TLS library in your own projects, follow these steps:
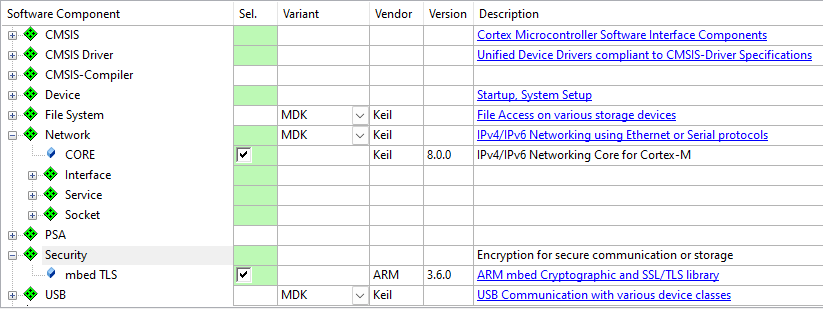
mbedTLS_config.h file.The Network Component offers secure software components that are using Mbed TLS. The user of the Network Component does not see the Mbed TLS API as it is hidden by the standard API of the secure component.
The following components are currently available in a secure variant:
To be able to communicate securely, you will need to generate appropriate certificates for the server. The section Creating your own certificates and keys explains how to achieve this for the secure components by using additional tools that are part of the Network Component.
The web server and the compact web server have secure variants available. The example HTTPS Server implements the secure Web server.
Note
- The first connection might take a while (a few seconds up to 10s) and depends on the browser and how many sockets/sessions it initially opens (differs in Edge, Chrome, Firefox, etc.). This delay is normal and due to the time required for asymmetric cryptography calculations on the target. After the initial delay, the HTTPS server works almost as fast the HTTP server.
- Your browser will complain during the connection that the certificate has a problem or is not trusted. You will need to add the certificate to your browser's trusted certificate storage manually.
- Do not use the test certificate in productive environments as it is not secret. Before shipping your product, make sure that you have added your own certificates and keys.
The Network Component's HTTPS service adds the file Net_Security.c to the project. This file contains generic test keys/certificates which enable the application to run out of the box. If you want to adapt the keys/certificates to your needs, you need utilities gen_key and cert_write which are available as part of the Arm MDK-toolbox.
The certificates and keys are generated using bash shell commands:
Generate random CA and Server Private Keys
Generate Self-signed CA Certificate
Generate Server Certificate
The certificates and crypto keys are created and their contents must be copied to the file Net_Security.c:
ca.crt into the array NetSecurity_ServerCA[], with a leading " and a trailing \n" inserted for each line.server.crt into the array NetSecurity_ServerCert[], with a leading " and a trailing \n" inserted for each line.server.key into the array NetSecurity_ServerKey[], with a leading " and a trailing \n" inserted for each line.Code Example
ca.crt
Net_Security.c
Note for Windows users
- You must add the test CA certificate
ca.crtto the Trusted Root Certificate store on your computer to avoid the Your connection is not private error in the Chrome or Microsoft Edge browser.- You need administrator rights for adding a certificate.
- To install a
ca.crtcertificate on your computer, double-click on it and select Install Certificate..., then select Local Machine for the store location.- Select Trusted Root Certification Authorities as the location for the certificate.
The e-mail client is available in a secure variant. The SMTPS Client example implements the secure email client.
The SMTPS service of the Network Component adds the Net_Security.c file to the project. This file contains an empty section for the e-mail server root CA certificate, so you cannot initially build the application. You must provide a valid root CA certificate for the server that you use to send e-mail. The certificate must be provided in PEM-encoding. Copy the contents of the certificate into the NetSecurity_EmailServerCA structure in Net_Security.c and add a leading " and a trailing \n" to each line.
Verifying the e-mail server is required by default to increase e-mail security. If you do not want to verify the server, you can disable server verification by defining the SMTPS_SERVER_VERIFY_NONE in your project (C/C++ define).
Note It is not necessary to create your own certificates or keys to send secure e-mail using SMTPS.